Cutting-edge EUC services & end-user computing tools to elevate your financial risk compliance
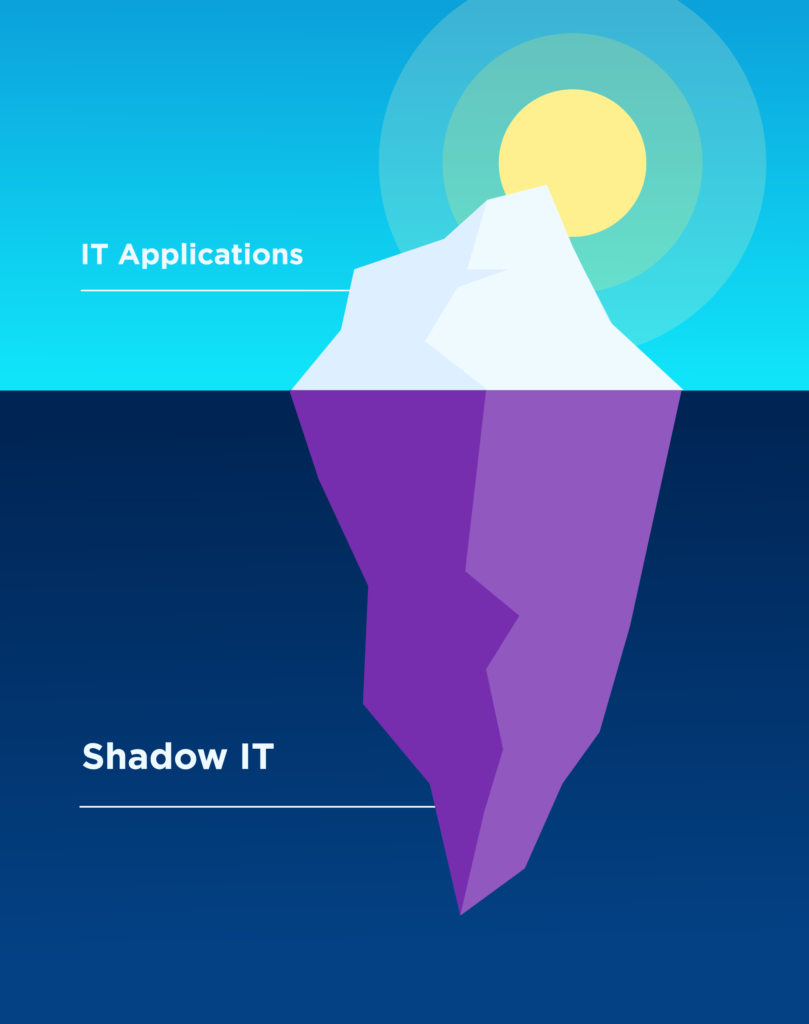
With the rise of globalization, distributed workforces, and increased regulation, taking control of your Shadow IT and EUC risk has never been more important.
ClusterSeven shines a light into hidden, sensitive spreadsheets, applications, and data that lie out of IT’s control and pose risk, helping you efficiently capture, monitor, and update one centralized inventory. Offering better visibility and control over your full portfolio of applications — including things like permission settings, update tracking, version control, and more — ClusterSeven makes it faster and easier for your organization to meet audit requirements, comply with regulatory updates, and mitigate risk before it makes an impact.

Build defensible EUC compliance with ClusterSeven

Keep a complete inventory of your EUC estate
Classify the risks associated with your newly discovered EUC files and organize them in a centralized database. Once you’ve established the spreadsheets your organization is using, you can carry out a deeper risk analysis on critical files using rules that matter to your business, such as the complexity of a formula or macro, use of sensitive terms in the file like “confidential,” inclusion of unprotected client or personal data, or the presence of hidden worksheets.
Monitor and track access and changes
Easily monitor who’s making changes — and to which files — by deploying workflows and alerts within your central EUC environment designed to help you meet audit and compliance requirements. Know exactly when these files were created or modified and who took those actions using role-based security permissions. And don’t worry about having too many spreadsheets or EUCs; ClusterSeven can handle over 100,000 files in a single database.


Satisfy regulators and stakeholders
By creating a control framework for your spreadsheets and databases, you’re establishing a defensible compliance program that can satisfy the requirements of various regulatory bodies. ClusterSeven can assist with managing the review and approval process for critical cells in high-risk or high-stakes spreadsheets and can automate the production of documentary evidence for different regulation requirements with its robust reporting dashboard. ClusterSeven helps satisfy the requirements of a variety of regulations including Sarbanes-Oxley (SOX), SMCR, OpRes, data privacy regulations like GDPR, SS 3/18, and SR 11-7 and is agile enough to adapt to any changes in the regulatory obligations.
Ready to mitigate Shadow IT and EUC risk once and for all?
Gain peace of mind and compliance with ClusterSeven
Robust, customizable, and scalable end-user computing tools for the modern enterprise

Discover every hidden spreadsheet and EUC across your enterprise
The Discovery tool does just what it says – allows organizations to discover all the spreadsheets and EUC assets (even those that are hidden), assess them, and understand how they’re connected.

Manage your business-critical spreadsheets from a single platform
The ClusterSeven Enterprise Spreadsheet Manager provides one central platform for the management of business-critical spreadsheets and supports the complete spreadsheet management lifecycle.

Leverage the same power of Shadow IT Manager — but in the cloud
Get the same level of transparency and control for cloud-based data as you get for EUCs by deploying our Cloud Spreadsheet Manager.

Centrally manage your EUC inventory with IMS
The ClusterSeven Inventory Management System stores all your business-critical spreadsheets and other key applications in a single, secure place.
Gain insight into your Microsoft Access databases with ADM
The Access Database Manager supports governance processes for assessing and reducing risk associated with Access databases, by applying a database control framework and lifecycle management to them.

Manage your script-based EUCs with one powerful, central platform
TSM provides a central platform for version and change management of your script-based EUCs, and delivers the equivalent transparency and control that ESM and ADM do for spreadsheets and access databases respectively.
“[ClusterSeven is] the only conceivable way that we can comply and mitigate spreadsheet risk.”
Donna Bradley, Head of Operational Risk at Shawbrook Bank Limited

Learn how organizations across the globe mitigate EUC risk with ClusterSeven.

See how automating spreadsheet control and attestation processes at Rabobank delivered improved regulatory compliance.

Learn how BlackRock, one of the world’s pre-eminent asset management firms, used ClusterSeven to address the requirements of their Global Spreadsheet Policy and assign risk metrics to prioritize spreadsheet remediation efforts.
Hear how Sumitomo Mitsui Banking Corporation brought governance to its spreadsheet landscape.
Do you have the full picture of your Shadow IT and EUC risk?
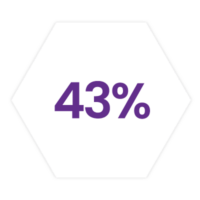
of spreadsheets have errors

of spreadsheets have errors

of spreadsheets have errors
ROI Calculator
Cost per year of maintaining spreadsheets:
$865,385
Estimated efficiency improvement after implementing ClusterSeven
50%
(This estimate is based on the operational efficiency in daily operations as well as transparency for compliance and audit by automating the creation, audit, and alerts on the changes to the structure, functionality, and data within a spreadsheet.)
Total savings:
$432,692
See What’s New with ClusterSeven: Mitratech’s GRC Community & Resources

The RegTech Report
This podcast is the go-to source for all things RegTech including RegTech news, insights from industry pioneers, and updates on the latest tech.
The Mitratech Morning Show
Tune in every month for an exciting conversation on a new GRC use case with one of Mitratech’s industry experts.
Decommissioning EUCs: A best practice guide
Get a practical framework for identifying EUCs that are suitable for decommissioning, and the best practices you need to employ to accomplish this.
Building a business case for EUC projects
We joined forces with Chartis to discuss the role of EUC application in moder://n businesses and explore the risks, reputation and cost overheads of EUC applications, before considering the returns to be gained by the use of ClusterSeven solutions to manage the EUC landscape.
ClusterSeven resources
Your quick solution to EUC risk
ClusterSeven is an information governance platform designed to help businesses identify potential risks across digital assets and ensure regulatory compliance across governance processes. IT professionals can access various unidentified end-user computing (EUC) spreadsheets, data assets, or applications.
ClusterSeven is designed to help businesses across various industry sectors, such as financial services, technology, manufacturing, law firms, human resources (HR), retail, energy and utilities, pharmaceutical, and legal. The software also lets users handle the entire spreadsheet management lifecycle, from document creation and storage to file retirement and replacement.
ClusterSeven allows enterprises to organize discovered EUC files based on associated risks and store them in a built-in database for future reference. Managers can configure workflows and role-based permissions for specific users, enabling them to access the version history of documents and receive automated alerts about file modifications. Using the reporting dashboard, supervisors can streamline approval processes for confidential or high-risk spreadsheets in compliance with various regulatory standards, such as GDPR, Sarbanes-Oxley (SOX), OpRes, SS 3/18, SR 11-7, and more.
“Shadow IT” refers to the hundreds or even thousands of End User Computing (EUC) spreadsheets and other data assets hidden across your enterprise, created by employees using applications that are outside of IT’s development and management process; Excel spreadsheets are one of the most common examples.
ClusterSeven locates the spreadsheets and EUC applications in use across your organization, identifies the relationships between them and their data lineage, and assesses the risks associated with them. You’ll gain transparency into what files you have, who owns each one, and which areas of the business use them.
Explore Mitratech’s Comprehensive GRC platform portfolio
Best-in-class, scalable solutions to help elevate your risk management, responsiveness, resilience, and reputation.